
Most people’s best and oldest friends are from our early schools days. DeVos is known to take the life long pleasure of socialization so that if a child or parent signs in online for 1 minute the “privateering school” seems legally is entitled to steal tax payers money. If tax dollars earmarked for education go to pay for private homes of girlfriends instead of education, it should be wrong. But DeVos disagrees and the GOP gives her free reign to create theft rings. More
Eli Broad who sponsors the best and most high performing charter schools in the country tried to stop her plan to defraud the public much like her brother Eric Prince did with his billions Dollar thefts in war of Iraq with his privateering military company Blackwater. To this day Eric Prince finds it offensive that people hold him accountable as to how he spent taxpayers money. Eric Prince said in recent interviews in an Alt-Right media company that he should not be accountable because the missing Billions and Billions of dollars were spent in a “private” military company and therefore he should not have to disclose the where the missing money went nor where it is now.
The only lesson the public can learn is how bottomless the sense of entitlement has become under our dysfunctional government that provides no oversight and no accountability of how and where our rapidly disappearing taxes and pensions has become. Unrepentant thieves have overthrown the government. DeVos will be a disastrous example of self righteous thievery of billions of taxpayers money due to funneling American public funds into “private” pockets. Another billion dollar heist is underway and sanctioned by Paul Ryan and McConnell. No wonder they want to silence the voices of reason.
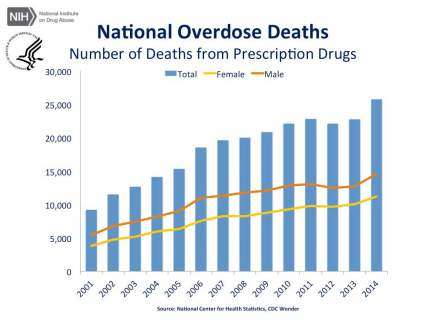
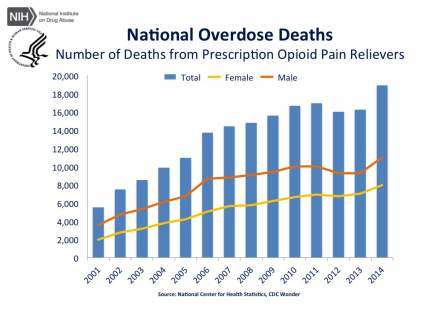 National Overdose Deaths—Number of Deaths from Prescription Opioid Pain Relievers. The figure above is a bar chart showing the total number of U.S. overdose deaths involving opioid pain relievers from 2001 to 2014. The chart is overlayed by a line graph showing the number of deaths by females and males. From 2001 to 2014 there was a 3.4-fold increase in the total number of deaths.
National Overdose Deaths—Number of Deaths from Prescription Opioid Pain Relievers. The figure above is a bar chart showing the total number of U.S. overdose deaths involving opioid pain relievers from 2001 to 2014. The chart is overlayed by a line graph showing the number of deaths by females and males. From 2001 to 2014 there was a 3.4-fold increase in the total number of deaths.

